Advanced Security Configurations
Zoho Mail is a secure email and collaboration platform that allows administrators to configure advanced security and encryption settings through the Zoho Mail Admin Console. Listed below are the advanced security configurations available:
BIMI
Brand Indicators for Message Identification (BIMI) is an email authentication technique which displays your brand's logo in the recipient's inbox against the emails you send. BIMI is an evolving email security protocol and is currently supported by very few email providers. Displaying your organization's logo in the emails you send increases the authenticity of the email and the trustworthiness of your brand. Email clients that support BIMI will automatically display your logo once you complete the BIMI configuration.
Mandatory settings before configuring BIMI
As an administrator, there are a few mandatory configurations that you should complete before you can set up BIMI.
- Set up MX, SPF, DKIM and DMARC for your domain.
- Upload your brand logo to a public web server as per the recommendations.
- Generate a Verified Mark Certificate (VMC) for your logo.
- To obtain the Verified Mark Certificate (VMC) from BIMI-accredited certificate providers, it is essential that your brand's logo is a legitimate trademark of your organization.
- Ensure that the VMC license subscription is active.
- DMARC needs to be set up with the action to be taken when DMARC validation fails (Quarantine or Reject), and the policy percentage needs to be 100%.
BIMI Logo Recommendations
The logo you upload for BIMI authentication should comply with the standards specified by BIMI. The image must be in the specific Scaled Vector Graphics (SVG) profile used by BIMI. Remember the guidelines given below while creating the BIMI image:
- Set the baseProfile attribute to "tiny-ps" and the version attribute to "1.2".
- Enter your organization's name in the title element and an optional description in the desc element.
- Ensure there are no external links or references (other than the specified XML namespaces).
- Keep the image centered with a square aspect ratio for better compatibility while displaying in the emails.
- The image size should be less than 32 KB.
- The background should be a solid color.
- Do not add scripts, animations or other interactive elements.
- Do not include x= or y= attributes within the <svg> root element.
Refer to the BIMI logo guidelines for more details.
Configure BIMI in Zoho Mail Admin Console
Once you complete the mandatory configurations, upload BIMI logo and generate a valid VMC, follow the below instructions to configure BIMI:
- Log in to Zoho Mail Admin Console and select Domains on the left pane.
- Select the domain for which you want to configure BIMI.
- Navigate to Email Configuration and select BIMI.
- Enter the BIMI logo URL which you published on the web server.
- Enter the VMC URL to prove ownership of the logo. The VMC file needs to be in a .pem format and hosted on the web.
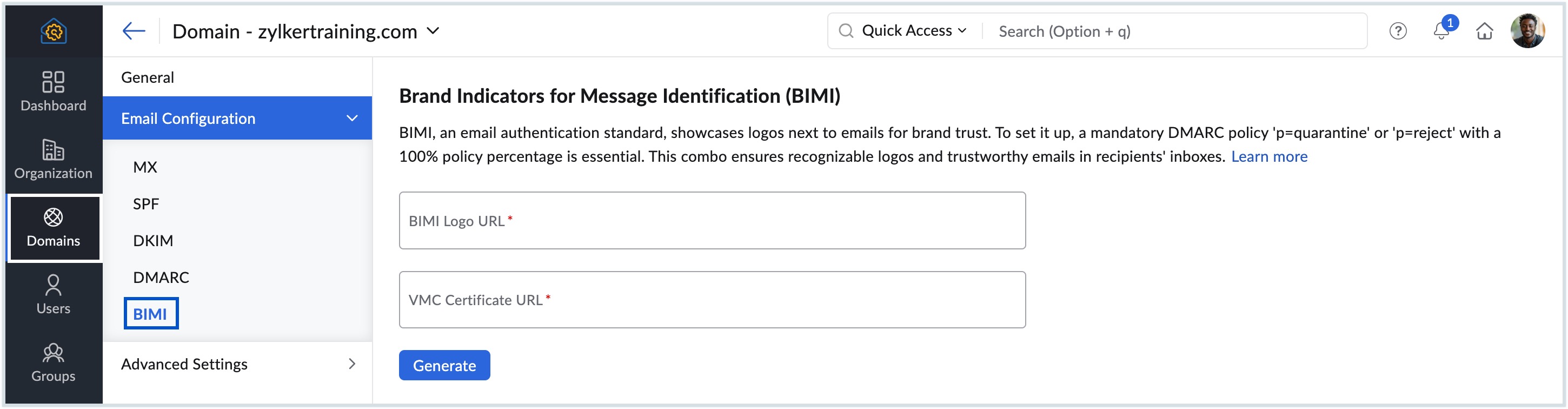
- Click Generate. The BIMI record for the select domain appears.
- Copy the BIMI record from the Admin Console.
- Log in to your domain provider's portal.
- Follow the steps to add a TXT record and publish the BIMI record in the Manage DNS page.
- Sample TXT value "v=BIMI1;l=[SVG URL]; a=[PEM URL]
- Navigate back to Zoho Mail Admin Console and click Verify BIMI record.
Note:
Your brand logo will be displayed in the end-user's inbox only if BIMI is supported by the recipient's email provider.